Email remains the primary entry point for cyberattacks targeting enterprises. As threats evolve from mass phishing to highly targeted business email compromise (BEC), organizations must carefully evaluate the email security tools they deploy.
For CISOs, IT leaders, and security managers, the goal is not simply to block spam. It is to protect financial transactions, safeguard sensitive data, ensure regulatory compliance, and maintain operational continuity. This blog explains what are email security tools, how they differ, and how to evaluate them strategically.
What Are Email Security Tools
Email security tools are technologies designed to protect email systems from phishing, malware, impersonation, account takeover, and data loss. They operate at different layers-gateway, cloud API, identity, user behavior, and response.
Rather than functioning as a single control, they form a coordinated defense that detects malicious content, verifies sender identity, monitors abnormal behavior, and reduces human-driven risk.
For a foundational overview of how these technologies fit into a broader strategy, refer to our Email Security Guide.
Why Enterprises Need Specialized Email Security Tools
Traditional spam filters are no longer sufficient against:
- Executive impersonation fraud
- Vendor invoice manipulation
- Credential harvesting attacks
- Conversation hijacking
- Cloud account takeover
Modern threats often contain no malware or suspicious links. They rely on social engineering and contextual deception, making intelligent detection capabilities essential.
Categories of Email Security Tools
When reviewing an email security tools list, it is important to understand that tools fall into distinct categories.
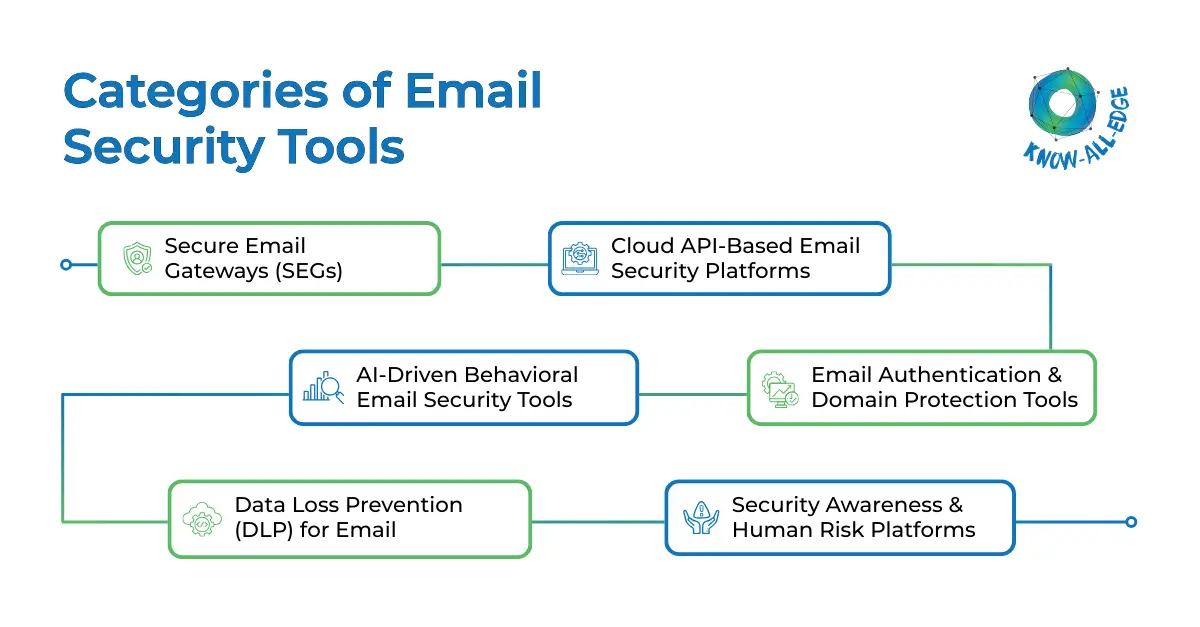
(1) Secure Email Gateways (SEGs)
These tools filter inbound and outbound email using rules, reputation scoring, and known threat signatures.
Best suited for:
- Blocking spam
- Detecting known malware
- Filtering malicious attachments
Limitation: Less effective against text-based BEC or advanced impersonation attacks.
(2) Cloud API-Based Email Security Platforms
Designed for Microsoft 365 and Google Workspace, these tools integrate directly via APIs rather than sitting at the perimeter.
Capabilities include:
- Post-delivery threat detection
- Behavioral analysis
- Automated remediation
They provide visibility into internal and lateral threats that traditional gateways may miss.
(3) AI-Driven Behavioral Email Security Tools
These solutions analyze communication patterns, writing styles, login behavior, and contextual anomalies.
Effective against:
- Business email compromise
- Executive impersonation
- Vendor fraud
- Account takeover attempts
This category is often considered when organizations ask, “What is the best tool for email security against BEC?” The answer depends on risk exposure, but behavioral detection is increasingly critical.
(4) Email Authentication & Domain Protection Tools
These focus on implementing and enforcing:
- SPF
- DKIM
- DMARC
They help prevent domain spoofing and protect brand reputation.
(5) Data Loss Prevention (DLP) for Email
DLP tools monitor outbound emails to prevent accidental or malicious data exfiltration.
Common use cases:
- Protecting financial data
- Preventing PII exposure
- Supporting compliance mandates
(6) Security Awareness & Human Risk Platforms
While not traditional filtering tools, these platforms reduce risk by training employees to identify suspicious activity.
They address the human element-often the weakest link in email security.
How to Evaluate an Email Security Tools List
When comparing a list of email security tools, decision-makers should evaluate:
- Detection capability beyond signature-based filtering
- Coverage for BEC and impersonation attacks
- Cloud-native integration
- False positive rates
- Ease of deployment and management
- Incident response and remediation automation
- Alignment with regulatory requirements
The objective is not to purchase the most feature-rich tool, but to select controls aligned with organizational threat exposure.
Choosing the Best Tool for Email Security: Strategic Considerations
There is no single “best tool for email security” for every enterprise. The right approach depends on:
- Industry risk profile
- Email platform (on-prem vs cloud)
- Volume of financial transactions
- Vendor communication exposure
- Internal security maturity
In many cases, organizations combine gateway protection, behavioral detection, authentication enforcement, and user awareness programs to address diverse risks.
For deeper insight into implementation approaches and technology alignment, explore our perspective on Email Security Solutions.
Common Enterprise Email Threat Scenarios
Understanding threat scenarios helps clarify tool selection.
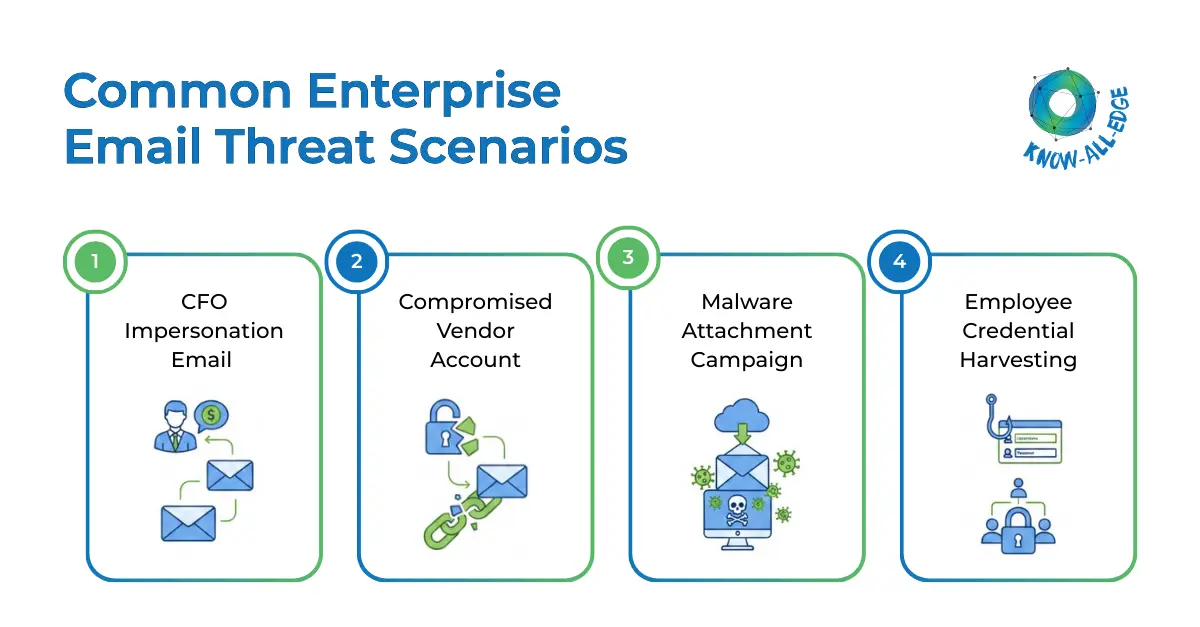
Scenario 1: CFO Impersonation Email
A threat actor spoofs a CEO and requests urgent wire transfer approval.
→ Behavioral detection tools identify unusual language and financial urgency.
Scenario 2: Compromised Vendor Account
An attacker hijacks a supplier’s mailbox and changes bank details.
→ AI-based anomaly detection flags deviation in payment instructions.
Scenario 3: Malware Attachment Campaign
A broad phishing campaign delivers infected documents.
→ Secure email gateways block known malicious signatures.
Scenario 4: Employee Credential Harvesting
A fake Microsoft login page captures credentials.
→ URL analysis and behavioral monitoring detect suspicious login patterns.
How We Help
Selecting and implementing the best tool for email security requires a structured evaluation of current controls, threat exposure, and operational workflows.
We help organizations assess their email security posture, identify gaps across gateway filtering, behavioral detection, authentication standards, and human risk management, and design a strategy aligned with business objectives.
Our approach is vendor-neutral and risk-focused—ensuring that technology decisions are driven by security outcomes, not product marketing. Whether you are reviewing your current stack or evaluating new Email Security Solutions, we provide practical guidance, implementation support, and strategic advisory services tailored to enterprise environments.
Conclusion
Email continues to be the most exploited communication channel in the enterprise environment. As threats evolve from mass phishing campaigns to targeted impersonation and business email compromise, selecting the best tool for email security becomes a strategic decision rather than a purely technical one.
No single solution addresses every risk. Organizations must evaluate tools based on their threat exposure, cloud adoption, financial workflows, and internal security maturity. By aligning technology choices with real-world attack scenarios, enterprises can reduce operational disruption, protect sensitive data, and safeguard business reputation.
Ultimately, effective email security is not about deploying more tools. It is about deploying the right tools with clarity, integration, and purpose.
FAQs: Email Security Tools
What are email security tools?
Email security tools are technologies that protect email systems from phishing, malware, impersonation, and data loss through filtering, authentication, and behavioral analysis.
What is the best tool for email security?
There is no universal best tool. The ideal solution depends on organizational risk profile, cloud usage, and exposure to financial fraud or impersonation attacks.
Do organizations still need secure email gateways?
Yes. Gateways remain effective for blocking spam and known malware, but they should be complemented with advanced detection capabilities.
How do AI-based security tools differ from traditional ones?
Traditional tools rely on known signatures and rules. AI-driven tools analyze behavior and context to detect previously unseen threats.
Are cloud email platforms secure by default?
Cloud platforms provide baseline security, but additional tools are often required to defend against advanced social engineering.
What role does DMARC play in email security?
DMARC helps prevent domain spoofing and protects brand reputation by enforcing email authentication policies.
Can email security tools prevent business email compromise?
Advanced behavioral and anomaly-detection tools significantly reduce BEC risk, especially when combined with authentication controls.
